Web time usage analytics
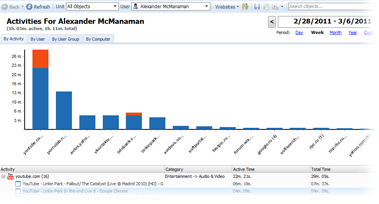
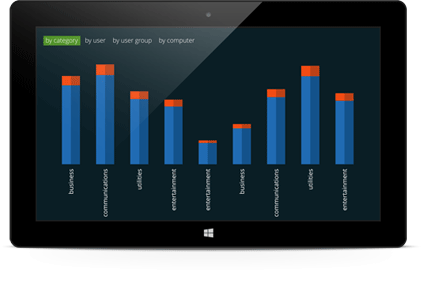
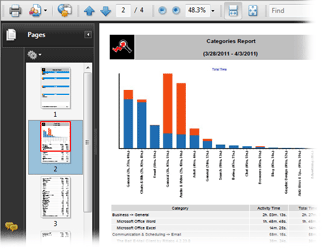
Our powerful analytics engine will give you a wealth of stats on how web surfing time at your company is distributed between users, computers, user groups, departments, sites, website categories and even by days of the week, dates and hours!
Unlike other Internet monitoring tools, Work Examiner not only collects data about the website address and the date of access, but it also calculates the amount of time that the user spent on the site (including active and idle time).
Web time usage analytics will give you answers to numerous questions such as these:

What websites do your employees devote the most time to?

Which of your employees spends the most time online?

Between which website groups is time online distributed?
Thanks to the huge website content database, you do not need to organize sites by groups — this is done automatically. If you still desire to anyway, you can arrange sites using 80 customizable built-in categories.
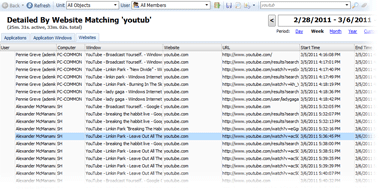
Detailed web access reports
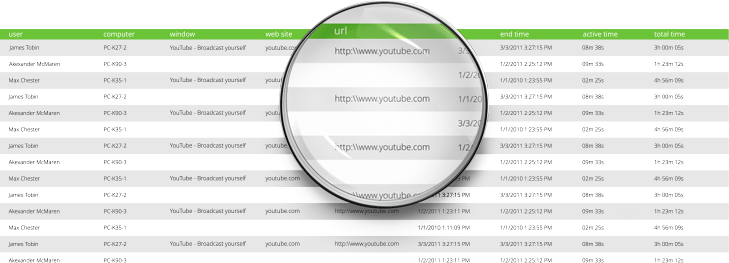
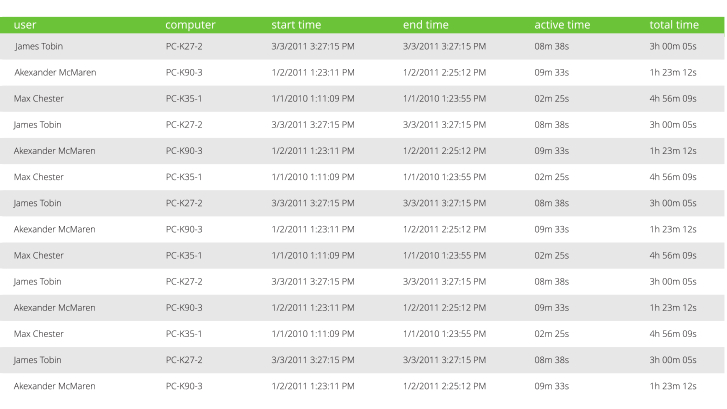
Work Examiner logs all HTTP/HTTPS requests, including them in a detailed web usage report with several parameters: user, computer, start time, end time, website, URL, window title and active/inactive/total time. Thanks to this report, you will always know who has visited which URL and when.
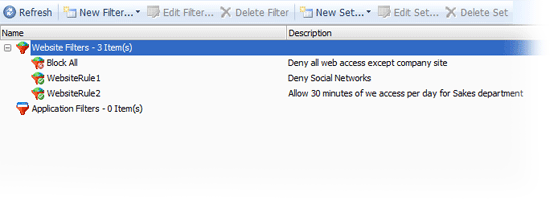
Web filtering
Web filtering works with any type of Internet connection. Web filtering rules allow you to:
Block sites by URL, content keyword, built-in category or URL mask
Use auto-updatable website content database with 2.300.000+ domains and 80+ categories
Block all sites except for specified ones
Specify users, user groups, computers and departments to apply the rule to
Apply web filtering rules to some or all employees
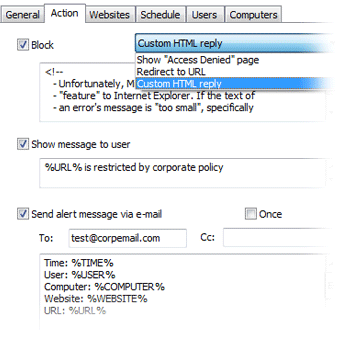
Show a custom “Access Denied” page
Redirect to your corporate website (or any other URL) instead of showing the “Access Denied” page
Apply a filtering rule with a delay
Do not block a site, but display an alert instead
Close TCP ports
Filter requests from specified programs only
Block HTTPS websites
- Do not block a site, but display an alert instead
- Close TCP ports
- Filter requests from specified programs only
- Block HTTPS websites
Web Access Alerts and Messages
 Get e-mail notifications when specified web sites are accessed, including the username, computer, time, URL and web filter action description (was the request blocked or not). The e-mail message text can be customized.
Get e-mail notifications when specified web sites are accessed, including the username, computer, time, URL and web filter action description (was the request blocked or not). The e-mail message text can be customized. Employees can also view a visible, customizable message when they access a restricted page. This is useful when a page is not blocked but you want to alert the user.
Employees can also view a visible, customizable message when they access a restricted page. This is useful when a page is not blocked but you want to alert the user. Any web rule can be applied with a delay and custom “before apply” messages can also be used. For example, every five minutes, users can see a message such as “You have 30 minutes of free web surfing remaining for today,” “You have 25 minutes of free web surfing remaining for today,” “...20 minutes...” and so on.
Any web rule can be applied with a delay and custom “before apply” messages can also be used. For example, every five minutes, users can see a message such as “You have 30 minutes of free web surfing remaining for today,” “You have 25 minutes of free web surfing remaining for today,” “...20 minutes...” and so on.Screenshots
Work Examiner allows you to view screenshots from a user's computer in real-time mode with constant refresh, almost like a spy cam. It can also take screenshots at regular intervals (every XX seconds) and save them in the database for later viewing. Then watch the saved screenshots just like a movie!
All screenshots can be exported as image files Black-and-white, 16-color and 256-color compressed JPEG formats are supported. When the user is idle, no screenshots are taken, in order to avoid excessive data capture Recorded screenshots include the active website, application name, window title and time info for quick searching.
Email capture
 Our email recording tool helps to reduce leaks of critical information and get a better idea of employee e-mail communications.
Our email recording tool helps to reduce leaks of critical information and get a better idea of employee e-mail communications.
 Work Examiner can capture and save every email message sent or received through the SMTP and POP3 protocols, as well as MS Exchange messages from MS Outlook.
Work Examiner can capture and save every email message sent or received through the SMTP and POP3 protocols, as well as MS Exchange messages from MS Outlook.
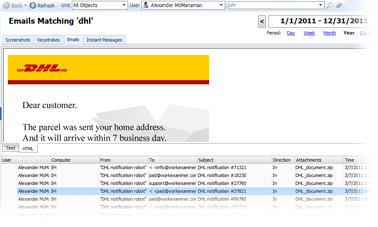
 All e-mail information — Time, From, To, Subject, Body and even Attachments — is captured. You can filter captured emails by any parameter or search messages for keywords.
All e-mail information — Time, From, To, Subject, Body and even Attachments — is captured. You can filter captured emails by any parameter or search messages for keywords.
Keystroke recording
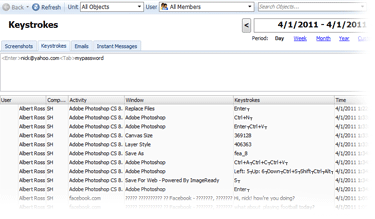
Keystroke recording captures every key that is pressed by the user. You will see what was typed in any program, whether it's IM chat, on a website, webmail or MS Word. You can even capture the passwords typed in many programs and websites!
All of the necessary items (User, Computer, Website/Application Name, Window Title and Date/Time) are recorded and available for quick searching and data filtering.
You can specify a list of programs to capture keystrokes from, such as web browsers, email clients and MS Office apps.
Both letters/numbers and special keys are recorded and displayed in a useful, easy-to-read style in the report.
IM recording
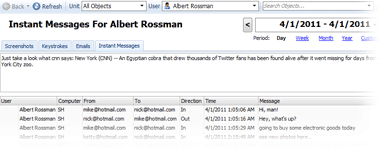
Our instant messaging capturing tool can record the most popular IM programs and protocols: Windows Live Messenger 2011, MSN, Google Talk, AIM, Yahoo Mesenger, ICQ and XMPP.
The User, PC, Date/Time and Message are all included in the report. You may search through all messages by keywords to discover what your employees are sharing.
100% stealth
Work Examiner Client works in stealth mode by default. This means that there are:
![]()
No icons in the taskbar
![]()
No entries in Start – Programs
![]()
No entries in Add/Remove Programs
![]()
No items in Task Manager – Applications
![]()
and even no items in Task Manager – Processes!
What's more, hidden WE Client modules are protected from being stopped.
Stealth technology works in both 32-bit and x64 environments.
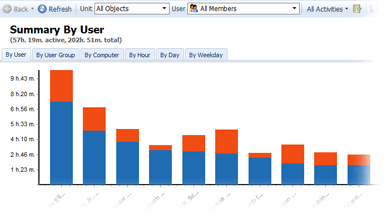
User activity reports
Find out what activities take up the most time at your company. Work Examiner allows you to combine or separate applications and web activities.
You will receive comprehensive, easy-to-read data on:

Who of your employees spends the most time on chat and playing games?

What part of the company's working time goes to employee fun and games?

Are employees using the computer...or are they distracted by other business?

Which users/departments are the most productive?
A number of user-friendly features will make the use of reports a snap:

Automatic activities categorization

Charts/bars/lines with drill-down support

Quick popup actions (block activity, see detailed data)

Quick report actions (search, create scheduled report, print preview, export)
Powerful data filtering capabilities can manage such report parameters as days, hours, days of the week, users, computers, departments, user groups, applications and websites, and display settings. Any parameter can be included or excluded from the report.
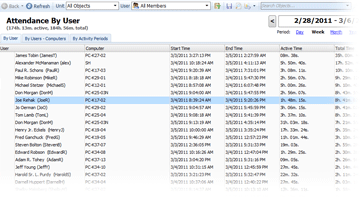
Attendance tracking
Work Examiner allows monitoring the attendance of your employees and their daily, hourly or weekly activity at the computer. Thus you can find out if anyone comes late, is absent from work, misuses the computer or leaves the workplace if their work should be carried out at the computer.
Get instant answers to the following questions:

Who comes late for work, who leaves early?
 Who and when used the computer without proper authorization?
Who and when used the computer without proper authorization?
 On what days does a particular employee spend more time at work, and what are the days the employee spends less time there?
On what days does a particular employee spend more time at work, and what are the days the employee spends less time there?

At what times are employees the most efficient?

How many hours a week has the employee worked?
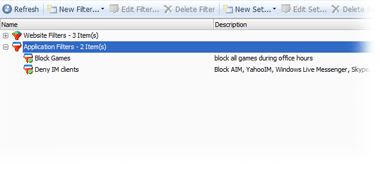
Application Filter
Application filtering allows blocking the start of applications for employees. You can block the start of certain applications or block running all applications except for specified applications. You can easily create a rule according to which employees will be able to start games only during breaks.
The Application Filter rules allow you to implement the following:
- Forbid running certain applications or categories (for example, games and instant messaging programs)
- Allow starting only specified applications or categories (for example, allow only MS Office applications to run)
- Specify the users, user groups, computers and departments to apply the rule to
- Forbid running applications at specified times (for example, during working hours)
- Show a custom message when restricted apps are launched
- Apply a filtering rule with a delay
- Specify an application name mask to filter all versions of a program (versions are usually a part of the name)
- Send an email alert to the admin or manager
- Alert only, without blocking
Current Activity
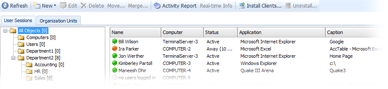
With the Current Activity feature, you can see which employees are working at the moment, what websites they are visiting, and what applications are being used. You can also view the status of each employee: whether the employee is working at the computer at the moment or not, and if not, for how long the employee has been away.
The organizational structure tree will help to easily find the employee that you are looking for.
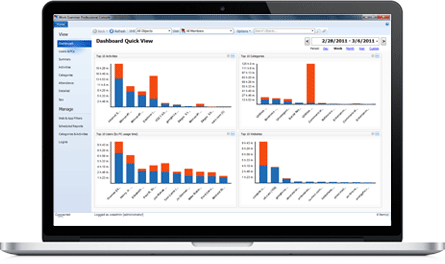
Dashboard
Just run Work Examiner and instantly see the most important data!
The Dashboard shows charts of the most critical reports. You can see any combination of reports in brief, add/remove reports, edit their advanced settings, drill down into the full report, export and print.
Each report bar can show a hint with detailed time usage information on the active, inactive and total time.
Security (Pro version only)
Work Examiner Professional allows multiple users to work with the WE Console simultaneously from different computers. Access rights can be set for each user, allowing the user to see only the information that he or she has access to.
For example, you can set Work Examiner Professional so that every manager can view Internet and application usage statistics for only his or her own employees.
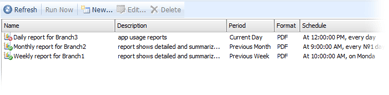
Scheduled Reports
Make Work Examiner work autonomously!
With Scheduled Reports you can:
 Configure the reports so that they cover a certain period: for example, managers will get the corresponding reports at the end of each week or month.
Configure the reports so that they cover a certain period: for example, managers will get the corresponding reports at the end of each week or month.
 Generate reports for specified users: for example, each manager will get reports on his or her employees' online and application activity.
Generate reports for specified users: for example, each manager will get reports on his or her employees' online and application activity.
 Set the format of reports: your managers will be able to get reports in a format that is useful for them and view the reports on any computer at a convenient time.
Set the format of reports: your managers will be able to get reports in a format that is useful for them and view the reports on any computer at a convenient time.
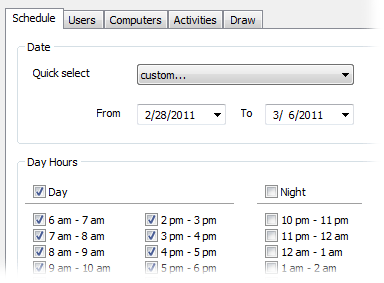
Extended data filtering
Any Work Examiner report can be sorted by:
Schedule: date range, days of week, hours
Activities: included and excluded applications, websites, activity categories (e.g., “Entertainment -> Adult”, “Business -> Sales”)
Users: included and excluded users, user groups, departments
Computers: included and excluded computers, departments
Display: manage view of charts, tables, columns, sorting and print preview page size.
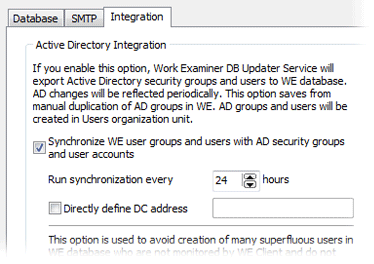
AD Integration (Pro version only)
No more manual entering of organizational structure data! Work Examiner will reflect your security groups and their contents automatically.
AD Integration can periodically synchronize and reflect a great deal of valuable data:
- Create WE users from AD data
- Update user display names
- Create user groups based on AD security groups
- Update user group members from the associated AD security group
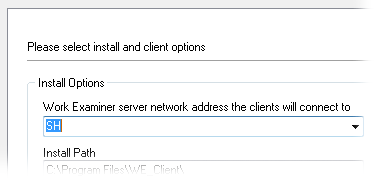
Remote client installation
Install Work Examiner clients in two clicks, remotely!
Work Examiner is a client-server application. WE Client must be installed on the employee’s PC. It can be easily and quickly distributed over the network. You can install client modules remotely and do not need to be present on the computers where the program is being installed.
If you have no admin rights, there is another solution: Client Builder.
Database optimization
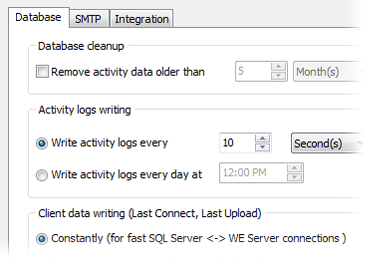
Database issues become more and more important when the amount of data increases from month to month. Here are a few ways to optimize database storage:
 Size control: Configure WE to delete all logs older than a specified number of days/months.
Size control: Configure WE to delete all logs older than a specified number of days/months.
 Smart data deletion: When you delete an object, the object is processed by a foreground service in parallel. This means no lags in the UI.
Smart data deletion: When you delete an object, the object is processed by a foreground service in parallel. This means no lags in the UI.
 Load management: Control the frequency of activity data updates and set the frequency of sending and size of client logs.
Load management: Control the frequency of activity data updates and set the frequency of sending and size of client logs.Using these options, you can enjoy a lightning-quick solution even when monitoring 1000+ PCs!
Client Builder
If you do not have admin rights, there is another solution to speed up deployment: build a custom WE Client setup package that already includes a WE Server address. The user simply runs it and WE is done!
This feature can also be used together with Active Directory group policies to deploy WE Client for many users.